Connecting remote IoT devices to a Virtual Private Cloud (VPC) on AWS securely is one of the most critical aspects of modern cloud-based infrastructure management. As more organizations adopt IoT technologies, ensuring secure communication between devices and cloud resources has become paramount. In this article, we will explore the best practices, tools, and configurations necessary to achieve a secure connection.
IoT devices generate vast amounts of data, and when integrated with AWS VPC, they can enhance operational efficiency. However, the security risks associated with remote connections cannot be overlooked. This article aims to provide a detailed roadmap for securely connecting remote IoT devices to AWS VPC, ensuring compliance with industry standards.
Whether you are a system administrator, cloud architect, or developer, this guide will equip you with the knowledge and practical steps to safeguard your IoT infrastructure while leveraging the power of AWS.
Read also:Best Knock Knock Jokes To Brighten Your Day
Table of Contents
- Introduction
- Understanding AWS VPC
- IoT Security Challenges
- Securely Connect Remote IoT Devices to AWS VPC
- Network Security Best Practices
- Data Encryption in Transit
- Identity and Access Management (IAM)
- Monitoring and Logging
- Scalability Considerations
- Best Practices for Secure IoT Connections
- Conclusion
Introduction
As the Internet of Things (IoT) continues to expand, organizations are increasingly relying on cloud platforms like AWS to manage their IoT infrastructure. Securely connecting remote IoT devices to AWS VPC is essential for maintaining data integrity and protecting sensitive information. This section will provide an overview of the importance of secure IoT connections and the role of AWS VPC in facilitating them.
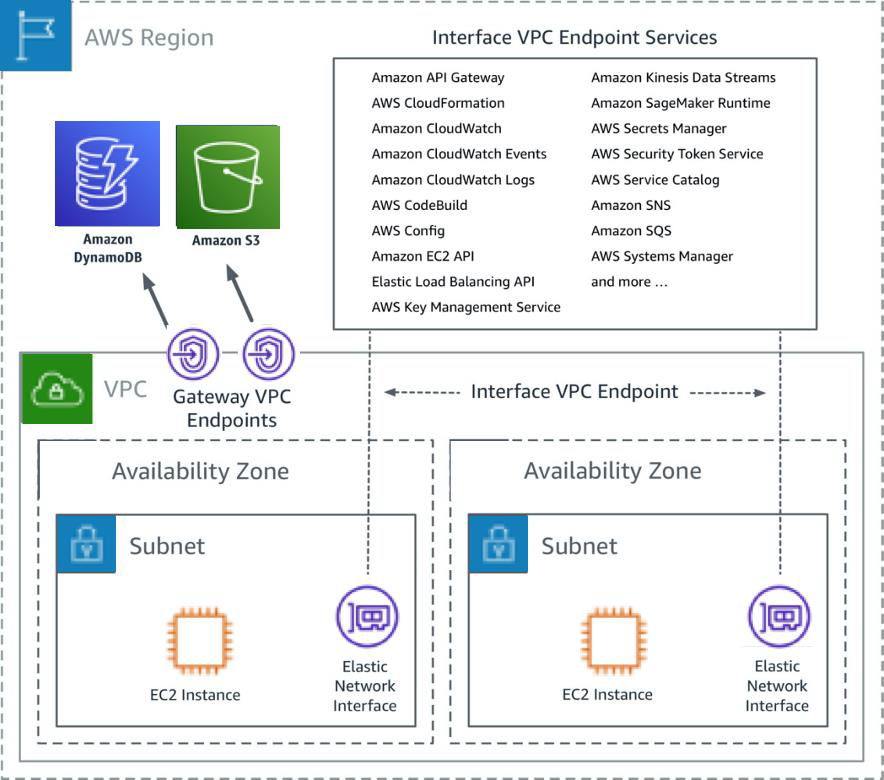
AWS VPC offers a robust framework for isolating resources and controlling access, making it an ideal solution for securing IoT devices. By leveraging AWS's advanced security features, organizations can ensure that their IoT infrastructure remains protected from unauthorized access and cyber threats.
Understanding AWS VPC
What is AWS VPC?
AWS Virtual Private Cloud (VPC) is a logically isolated section of the AWS cloud where you can launch AWS resources in a virtual network that you define. It enables you to customize your networking environment, including IP address ranges, subnets, route tables, and network gateways.
Key features of AWS VPC include:
- Private IP address ranges
- Subnet creation
- Internet gateways
- Security groups and network access control lists (ACLs)
Why Use AWS VPC for IoT?
Using AWS VPC for IoT provides several advantages, including enhanced security, better control over network traffic, and seamless integration with other AWS services. By configuring VPC settings appropriately, you can ensure that only authorized devices and users can access your IoT resources.
IoT Security Challenges
Securing IoT devices presents unique challenges due to their diverse nature and widespread deployment. Some of the most common challenges include:
Read also:Misty Foster Erome Unveiling The Intriguing World Of Erotic Literature
- Limited computational resources on IoT devices
- Difficulty in updating firmware and software
- Potential for unauthorized access through unsecured devices
To address these challenges, organizations must adopt a multi-layered security approach that includes network segmentation, encryption, and identity management.
Securely Connect Remote IoT Devices to AWS VPC
Step-by-Step Guide
Connecting remote IoT devices to AWS VPC involves several key steps:
- Set up a VPC with appropriate subnets and security groups
- Configure a virtual private gateway (VGW) for secure communication
- Establish a site-to-site VPN connection between the IoT devices and the VPC
- Implement IAM policies to control access to IoT resources
Tools and Services
AWS offers a variety of tools and services to facilitate secure IoT connections, including:
- AWS IoT Core
- AWS IoT Device Management
- AWS CloudWatch
Network Security Best Practices
Ensuring network security is crucial when connecting remote IoT devices to AWS VPC. Here are some best practices to follow:
- Use network access control lists (ACLs) to restrict traffic
- Implement security groups to control inbound and outbound traffic
- Regularly audit network configurations for potential vulnerabilities
By adhering to these practices, you can significantly reduce the risk of unauthorized access and data breaches.
Data Encryption in Transit
Why Encryption Matters
Encrypting data in transit is essential for protecting sensitive information as it travels between IoT devices and AWS VPC. AWS provides several encryption options, including:
- TLS/SSL for secure communication
- AWS Key Management Service (KMS) for managing encryption keys
Implementation Tips
When implementing encryption, consider the following tips:
- Use strong encryption protocols and algorithms
- Regularly rotate encryption keys
- Monitor encryption usage and performance
Identity and Access Management (IAM)
Identity and Access Management (IAM) is a critical component of securing IoT connections on AWS. IAM allows you to manage user access to AWS resources and enforce least privilege principles.
Key IAM Features
- User and group management
- Policy creation and assignment
- Multi-factor authentication (MFA)
By leveraging IAM, you can ensure that only authorized users and devices can access your IoT resources.
Monitoring and Logging
Importance of Monitoring
Monitoring and logging are essential for detecting and responding to security incidents in real time. AWS provides several tools for monitoring IoT connections, including:
- AWS CloudTrail for tracking API activity
- AWS CloudWatch for monitoring logs and metrics
Best Practices
To maximize the effectiveness of monitoring and logging, follow these best practices:
- Set up alerts for suspicious activity
- Regularly review logs for potential security issues
- Implement log retention policies to comply with regulatory requirements
Scalability Considerations
As your IoT infrastructure grows, ensuring scalability is critical for maintaining performance and security. AWS VPC supports scalable architectures by allowing you to:
- Add additional subnets and resources as needed
- Automate scaling using AWS Auto Scaling
- Optimize network configurations for high availability
By designing your architecture with scalability in mind, you can ensure that your IoT infrastructure remains robust and secure as it expands.
Best Practices for Secure IoT Connections
To securely connect remote IoT devices to AWS VPC, follow these best practices:
- Use strong authentication and encryption protocols
- Regularly update firmware and software on IoT devices
- Implement network segmentation to isolate sensitive resources
- Monitor and log all network activity for potential threats
By adhering to these practices, you can create a secure and reliable IoT infrastructure on AWS.
Conclusion
Securing remote IoT connections to AWS VPC is a complex but critical task for modern organizations. By following the best practices and leveraging AWS's advanced security features, you can ensure that your IoT infrastructure remains protected from cyber threats.
We encourage you to share your thoughts and experiences in the comments section below. Additionally, explore other articles on our site for more insights into cloud computing and IoT security.